Table of Contents
- Summary
- Network Validation Primer
- Report Methodology
- Decision Criteria Analysis
- Evaluation Metrics
- Key Criteria: Impact Analysis
- Analyst’s Take
- Methodology
- About Ivan McPhee
- About GigaOm
- Copyright
1. Summary
Regardless of the network size or type, ongoing configuration changes based on business and technical requirements are inevitable. However, network infrastructure is becoming increasingly complex with work-from-anywhere (WFA) initiatives, geographically distributed operations, and the addition of cloud-based services. Modern networks encompass a large number of edge devices, including firewalls, load balancers, routers, and switches. Adding a rack, upgrading the operating system (OS), or adding a border gateway protocol (BGP) peer or virtual local area network (VLAN) can cause an outage with significant business repercussions.
Moreover, with increasing security threats to network resources, enterprises must enforce robust practices, ensuring configuration and security policies remain compliant with a network source of truth (NSoT) based on the latest industry standards. Maintaining network compliance based on business, network, and security intent must be a priority for network administrators. However, making and keeping track of each change in a multivendor networking environment comprising hundreds or thousands of network devices is overwhelming.
As a result, organizations require a modern, disciplined approach to network change management, ensuring compliance across all network devices and services. Figure 1 depicts the network change management process required to maximize the uptime of business-critical applications and processes while enhancing the user experience. While scope determination, risk analysis, and peer review are manual processes, validating network changes both before and after implementation needs to be automated, accelerating the process and reducing risk by injecting consistency and discipline.
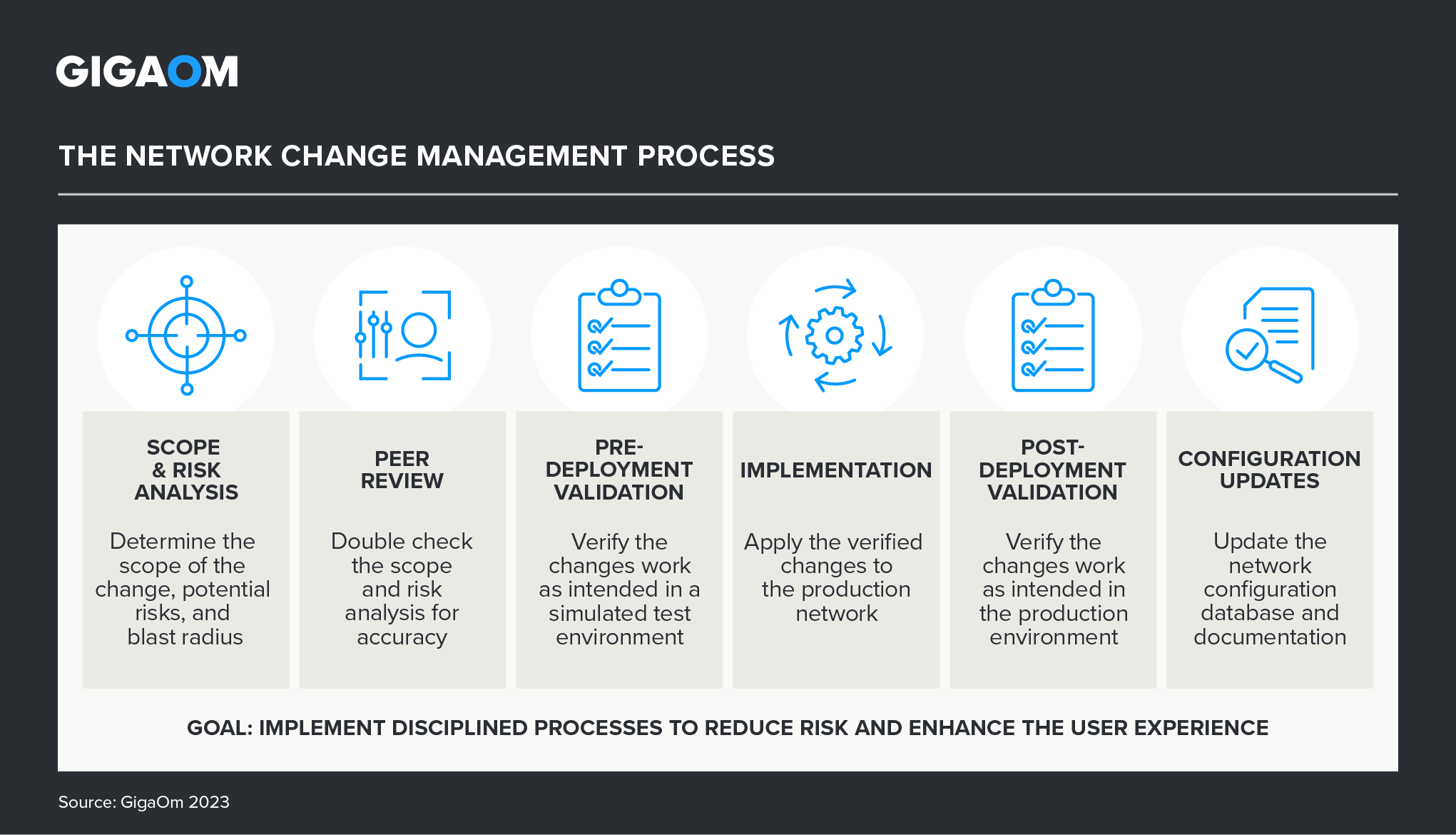
Figure 1. The Network Change Management Process
This is the second year that GigaOm has reported on the network validation space. This report builds on our previous analysis and considers how the market has evolved over the last year.
This GigaOm Key Criteria report details the capabilities (table stakes, key criteria, and emerging technologies) and non-functional requirements (evaluation metrics) for selecting an effective network validation solution. The companion GigaOm Radar report identifies vendors and products that excel in those capabilities and metrics. Together, these reports provide an overview of the category and its underlying technology, identify leading network validation offerings, and help decision-makers evaluate these solutions so they can make a more informed investment decision.
How to Read this Report
This GigaOm report is one of a series of documents that helps IT organizations assess competing solutions in the context of well-defined features and criteria. For a fuller understanding, consider reviewing the following reports:
Key Criteria report: A detailed market sector analysis that assesses the impact that key product features and criteria have on top-line solution characteristics—such as scalability, performance, and TCO—that drive purchase decisions.
GigaOm Radar report: A forward-looking analysis that plots the relative value and progression of vendor solutions along multiple axes based on strategy and execution. The Radar report includes a breakdown of each vendor’s offering in the sector.
